Smartphones contain a treasure trove of personal data, which makes them a worthwhile target for hackers. However, law enforcement is not above snooping on cell phones, and their tactics are usually much harder to detect. Cell site simulators, often called Stingrays, can trick your phone into revealing private communications, but a change in Android 16 could allow phones to detect this spying.
Law enforcement organizations have massively expanded the use of Stingray devices because almost every person of interest today uses a cell phone at some point. These devices essentially trick phones into connecting to them like a normal cell tower, allowing the operator to track that device's location. The fake towers can also shift a phone to less secure wireless technology to intercept calls and messages. There's no indication this is happening on the suspect's end, which is another reason these machines have become so popular with police.
However, while surveilling a target, Stingrays can collect data from other nearby phones. It's not unreasonable to expect a modicum of privacy if you happen to be in the same general area, but sometimes police use Stingrays simply because they can. There's also evidence that cell simulators have been deployed by mysterious groups outside law enforcement. In short, it's a problem. Google has had plans to address this security issue for more than a year, but a lack of hardware support has slowed progress. Finally, in the coming months, we will see the first phones capable of detecting this malicious activity, and Android 16 is ready for it.
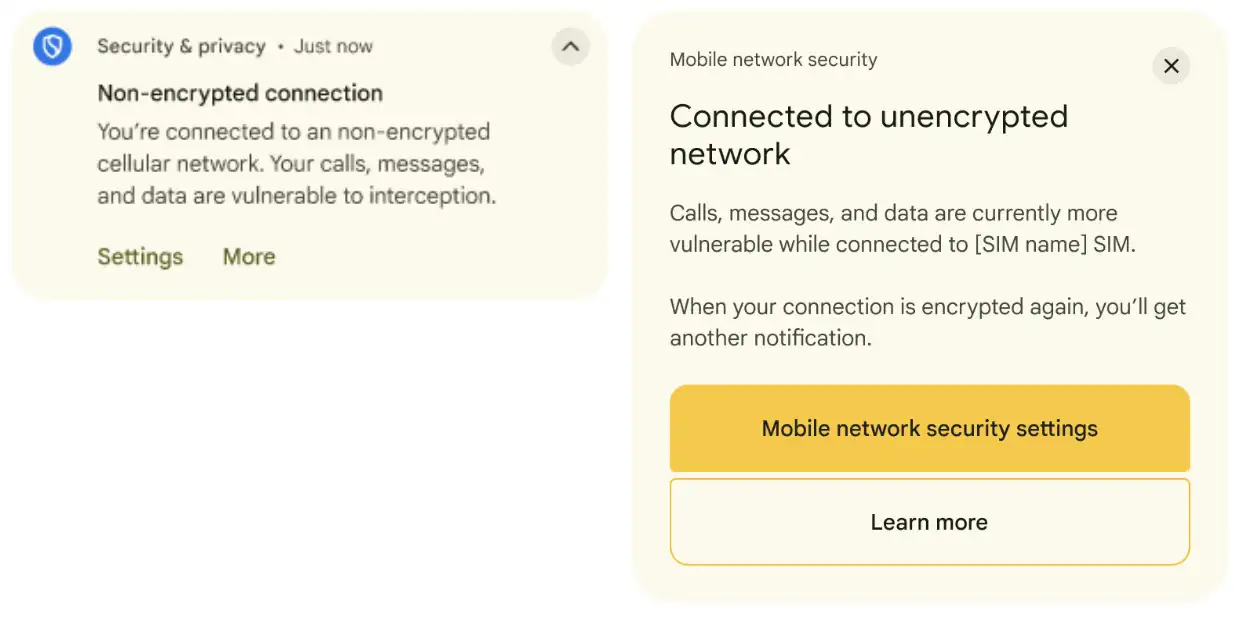
As part of Google's mobile network security features, Android phones will be able to detect when a network requests a unique identifier or attempts to force an unencrypted connection. This produces a "network notification" to warn of the potential attack. This settings page will also include a toggle to disable insecure 2G networks, which is already supported in Android.
The problem, however, is that no current phones can do this. To unmask fake cell towers, Android phones need to have version 3.0 of Google's IRadio hardware abstraction layer, which has to be supported at the modem level. Even Google's latest Pixel phones lack support, so the network security settings page is hidden in current builds of Android 16.

According to Android Authority, Google allows OEMs to lock in certain hardware features at the time of a phone's release. So it's unlikely any current phone will be updated with modem drivers that are capable of Stingray detection. Phones that launch on Android 16 later this year, like the Pixel 10, will be the first to call out fake cell towers. In the meantime, you can still disable 2G connections to limit the impact of cell site simulators.